The Cyber Why: What We Read This Week...
... and why you should too! (10/13/23)
Happy Friday the 13th! So sorry I’m late this week. I’ve been on the road traveling and haven’t had enough time to write. So much to do and so little time. This week we cover sad news out of Israel, discovering biases that could impact your day to day choices, how marketing terms build (or don’t build) markets, exits DO NOT always result in winners, and of course the old stand by “The cat did it!” All this and more in this weeks The Cyber Why! - BTW scroll to the bottom for some killer quick hit links as well!
The Next Cyber Why Featured Sponsor - YOU!
Sponsor The Cyber Why, a thriving blog intersecting technology, business, and cybersecurity. Connect with 2,800+ subscribers, including CISOs, founders, executives and tech enthusiasts, keen on market trends and investment insights through a cybersecurity lens. Secure your sponsorship slot in our weekly digest, aligning your brand with industry thought leaders.
Prayers to Israel - Stay Safe!
Israeli Tech Workers Prepare To Mobilize In Wake Of Attacks (Crunchbase)
Israel’s vaunted tech sector is going to war (The Washington Post)
This is a significant moment in the history of Israel. Over 360,000 Israeli residents have been called to active duty to fight against an invasion from the militant group Hamas located in the Gaza Strip. I do not and will not claim to know the history of the fighting, nor do I claim to understand, in the slightest, what this must feel like for those located in Israel. What I DO know is that my heart bleeds for all those involved in the fighting, who have lost loved ones, and who fear for their families and friends due to the conflict. The impact at a personal level is profound, and the impact on the technology sector will be as well. It’s believed that somewhere between 15-30% of technology workers, including founders and CEOs will be called up to fight, leaving many of the cybersecurity and high-tech companies in the region decimated on the staffing front. In times like these, the tech entrepreneurial community must come together and support our brothers and sisters who are going through hardships. I know many Israeli tech founders and employees and pray they all come through this with minimal damage to personal life and well-being. My thoughts and prayers are with all of you - you will come out stronger on the other side.
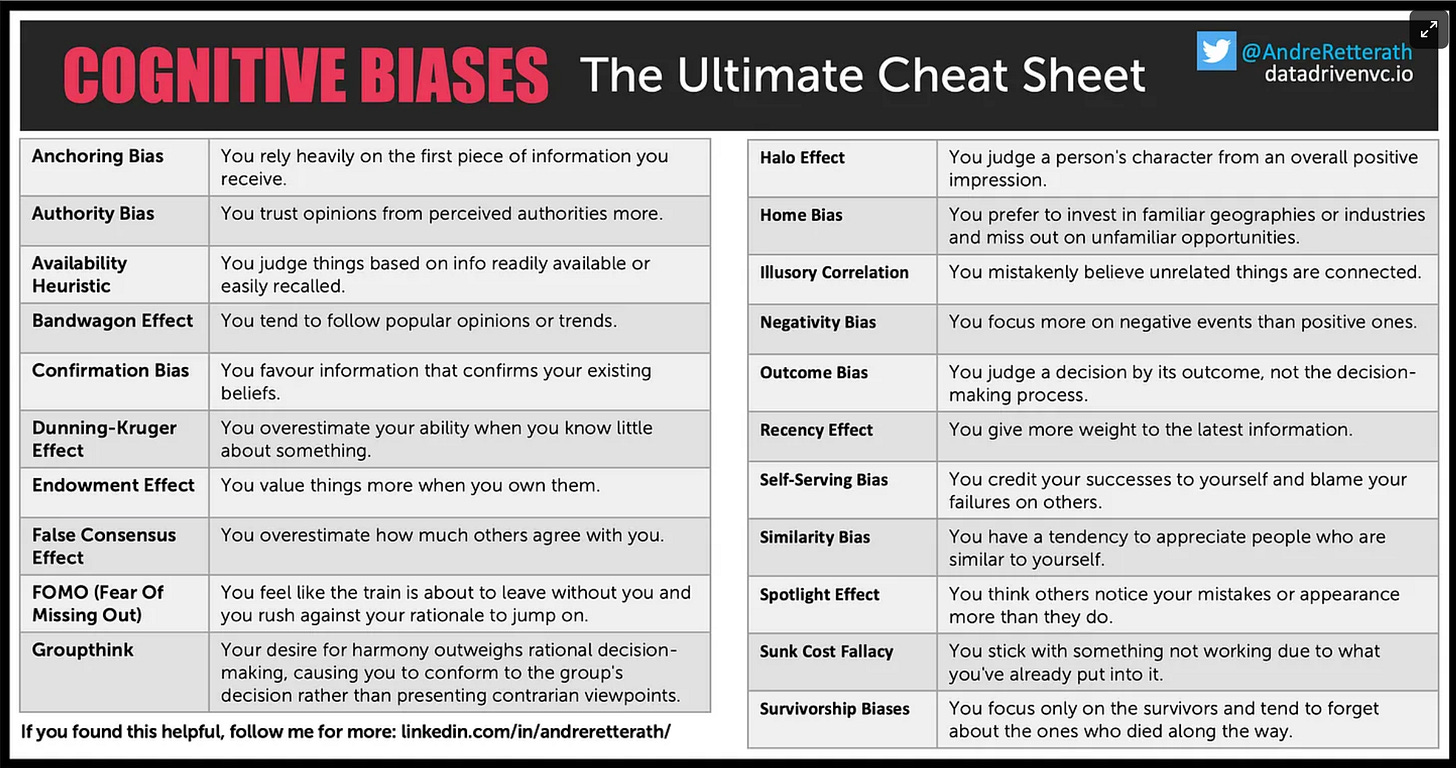
Learn Your Biases Improve Your Decisions
Whatever You Do, Be Aware of These 21 Biases! (Data-Driven VC)
I love the content created by the Data-Driven VC, Andrew Retterath. He takes a unique approach to venture capital that is both technically deep and open to community discussion. I typically get excited about his writing on the process around venture capital and using data to make informed choices, but what really caught my eye in this article was the cognitive biases ultimate cheat sheet. The decision-making process is full of issues, many of which are studied in detail in psychology and sociology circles. The first step to limiting the impact of biases on our choices is to be aware they exist. There is a good chance you know about a few of these, but I am positive you don’t know them all. Give the table a read-through and see if you can identify how many of the biases have impacted you recently in your daily life. I know I certainly found a few! If you want to understand how the biases impact venture capital choices, go do a deep dive into the article itself.
Marketing Terms Do NOT Make A Market (Or Do They?)
100 Most Common Phrases in Cybersecurity Media Coverage (TechNews)
Ever since my days as an analyst at Forrester Research, I have been interested in the predominant cybersecurity trends and why some turn into massive markets while others wither away into uselessness. I’ve made some great picks, and I’ve predicted success where none was to be found, but over the years, I’ve leaned into my research and listened to my gut, and chose more winners than losers. One of the less “accurate” but more “fun” ways of looking at trends is to analyze the "market buzz” about a specific area of focus. I spent some time thinking through the most common phrases in cybersecurity media coverage, and a few ideas rose to the top of my brain.
Regulations, hackers, and breach details continue to drive the FUD that fuels CISO and board-level cyber decision-making. No surprise here that these are at the top of the list. Sensationalistic headlines drive attention.
Authentication lands on the podium at #3 and is a pleasant surprise to see near the top. While this may be driven by beach details (multifactor? OKTA compromises? A&A commentary around ransomware stories?), many of the more modern ways of implementing cybersecurity in a distributed and cloud-centric environment center upon the authentication and authorization objects and processes. Whatever is driving this to the top, I’m glad to see it up there.
Some of the more technically exciting markets, such as security data lakes, SBOMs, threat hunting, and fraud detection, are in the bottom 30% of the buzz graph. Likely, this is because they are more challenging to write about, making them less attractive to a generic audience, OR they could be dud markets that nobody is going to care about in a year or two. Time will tell!
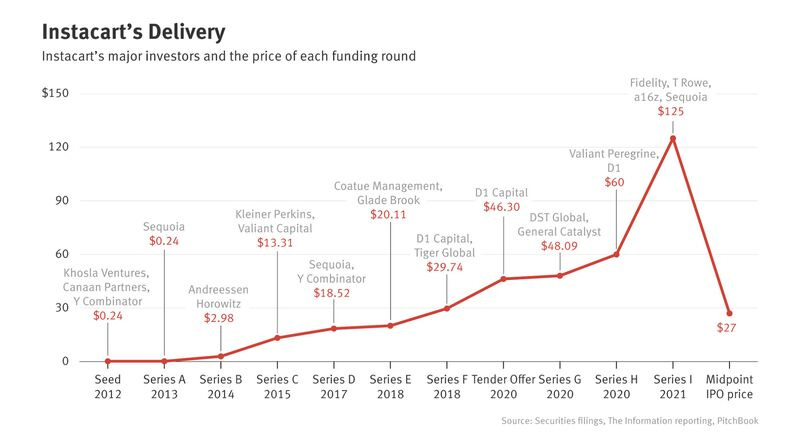
Loom and Instacart Winners and Losers
Investor Returns Breakdown For Loom (Phil Haslett)
Investor Returns Breakdown For Instacart (Yuechen Zhao)
When is an exit not a successful exit… when people lose money! Whenever a tech startup exits, people send congratulatory messages the founders, investors, employees of the company. Emails and DMs such as: “Yay, congratulations!” “When are you buying your new yacht?” “Are you interested in investing in my new idea?!” come flowing in from every acquaintance old and new. What people don’t quite understand is that in today’s era of down rounds, sales for lower valuations, preference stacks and recaps, not everyone ends up a winner. Research by Phil Haslett shows that in the case of yesterday’s acquisition of Loom by Atlassian everyone did ok with the latest money in coming from A16Z and resulting in a break even return. In the case of the Instacart IPO not everyone ran so hot. Some additional research by Yuechen Zhao shows that series D and later may have actually LOST money in their investment and the C round would have been better off if they had just invested in an S&P index fund with the money. You never really know who wins and loses and to what degree in an exit but I guess sometimes just the act of wrapping the project up is worthy of congratulations!
Blame The Cat. Everyone Will Believe THAT!
Cat accused of wiping US Veteran Affairs server info after jumping on keyboard (The Register)
In an updated version of the excuse, “the dog ate my homework”, a US Veteran Affairs technician tried to explain to a call of over 100 people that while reviewing the configuration of a system cluster configuration, his cat decided to rampage the keyboard and delete the file. The US Government has confirmed the incident but did not elaborate on the technical details of how the system was taken offline. While this could be a case of “feline blame transference,” I can’t imagine a scenario where I would get onto a call with over 100 of my peers and superiors and try to blame the cat for a mistake if it didn’t really happen. Either way, after being down for four days, the system was restored to “purrfect” operations. (Sorry, I couldn't resist the dad joke.)
Quick Hits and Hidden Gems
Should Startups Care About Profitability? (Mark Suster) - This throwback piece is rather timely regarding the new way of valuing startups. Has the pendulum swung too far back toward profitability?
What is Palo Alto Networks Doing? (Frank Wang $$$) - Frank’s content is worth paying for. Get his take on the Talon and Dig acquisitions by PANW here.
A shortage of cybersecurity founders building companies, not features or products (Venture In Security) - Building a business is not just products and features.
Sorry. My heart says yes, but my schedule says no (Dharmesh Shah) - Throwback to 2011. Something I need to focus on and get better at. Time is the most important resource.
Five Questionable Things About Top Ten Security Lists (Crash Override) - Mark doesn’t pull punches as he lambasts the OWASP (and other) Top 10 Lists as having little use other than to prop up vendor sales.
If you’ve made it this far, you either found our musings at least semi-entertaining, OR you enjoyed the pain and kept going regardless. No matter how you made it to this point, you should know that we appreciate you. Please do us a solid and share The Cyber Why with your friends. We would love to reach a bigger audience, and referrals are how we do it. Help us out, and we’ll see you next week!