After two full weeks of travel, one of which was Vegas for Hacker Summer Camp, I’m ready to dive back in and bring you our most exciting articles and stories of the week.
In this issue of The Cyber Why newsletter, we surface the “3 Billion People” hack that “may not be” at National Public Data, Tyler’s views on hitting the bottom of the VC investment cycle (tl;dr it’s up from here), the White House spends a whopping $11M on open source supply chain security (that’s all?!), measuring security debt as a new paradigm for understanding risk, and last but not least, what happens when a Tesla Cybertruck ends up in the hands of a Chechen Warlord (oh my!). All this and more in this week’s The Cyber Why!
The Cyber Why POD - Now in 4k! (To be fair, it always has been in 4k and high-quality audio. We’re tech nerds like that.)
TCW Newsletter and the TCW Podcast both have 2024 sponsorship slots remaining! If you are interested in reaching nearly 5k security-minded people a week via direct mail plus nearly 30K views per month, sponsor The Cyber Why. It’s inexpensive - I SWEAR! Email tyler.shields@gmail.com for more information.
A US-Wide Compromise That May Not Be Real
Inside the "3 Billion People" National Public Data Breach (Troy Hunt)
Is it real? The “billions of compromised accounts” question. A massive data breach involving National Public Data (NPD) has sent shockwaves through the internet, but the true extent and legitimacy of the leaked information remains a mystery.
Initially, hackers claimed to have stolen data on nearly 3 billion people, including sensitive information like Social Security numbers. However, as more details emerge, a complex puzzle forms. Different batches of data appeared online, varying in size and content. Some information seemed accurate, while other parts appeared to be random or even fabricated. As outlined by blog author Troy Hunt, the challenge lies in determining which data is genuine and which is simply noise added to create confusion. With conflicting reports and a lack of transparency from those involved, unraveling the truth about this breach is proving to be an arduous task. Thanks, Troy, for tracking this one down and providing a life preserver in a murky pond.
Venture Bottom or Death Spiral?
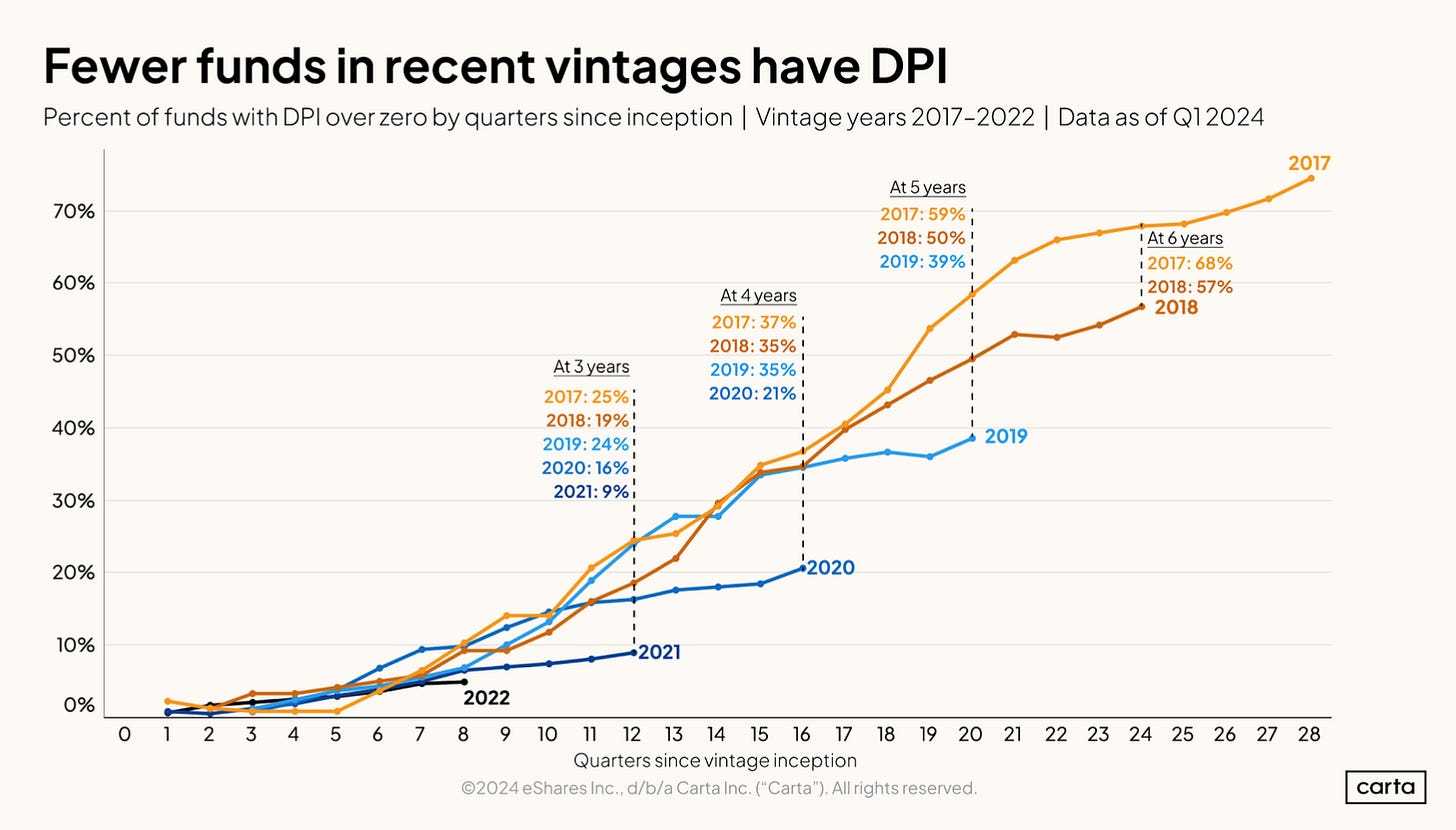
VC Fund Performance: Q1 2024 (Carta Report)
In an article posted on August 16th, the Carta data research team noted that venture capitalists are having a rough go of it. With interest rates soaring and IPOs as scarce as a meth head’s teeth, money managers are in dire need of returns. Based on a view into over 1,803 venture funds, Carta's latest report paints a really tough picture. Funds from 2022 have deployed only 43% of their cash after two years, the slowest pace ever. And don't even get started on returns – less than 10% of 2021 funds have seen a dime back from their investments after three years.
If you think things are bad for VCs, wait until you hear about the businesses they are funding. The data on graduation rates is downright depressing. Fewer and fewer seed-stage companies are making it to Series A, suggesting a sad outlook for many new ventures. Are we simply at the bottom of a venture down cycle, or should we be worried about something more drastic occurring? In my opinion, we should see a positive bounce over the next few vintages. Fingers crossed!
A Whole $11M for Open Source Security in Critical Infrastructure?!?!
White House details $11M plan to help secure open source (Cybersecurity Dive)
(Katie Pick) Last week during DEFCON 32, National Cyber Director Harry Coker Jr. revealed a plan by the White House and Department of Homeland Security (DHS) that will focus on helping secure open source software used in operational technology. Coker shared that the plan is to invest $11M USD in a program they’re calling the “Open Source Software Prevalence Initiative.”
Now, on the one hand, this is great! Any time initiatives like this come down from the top, it’s a signal to public and private organizations that it’s time to step up their game. In the case of open source — or open source-based — software, it’s past time. The threat surface is enormous. According to various sources, attacks on software, particularly those targeting the software supply chain, have increased by 300-400% in the last three years. Driven by increased reliance on open source codebases and the complexity of modern software development, there are no signs of these attacks slowing down. Given that critical infrastructure (CI) increasingly relies on traditional software (versus purpose-built, air-gapped components), the sector is at least as vulnerable to software and supply chain attack as any other industry (i.e., very high risk) or likely higher, given the impact of a CI compromise.
On the other hand, what does it say that the government is offering less than most seed rounds for organizations to make substantive changes in software development and open source security? Though this isn’t the only initiative or government-supplied help organizations can get in this realm, it feels a little like offering a single nail to fix a leaky bucket.
Security Debt - A Metric NOW With Meaning
Contextual Vulnerability Management With Security Risk As Debt (Ari Kalfus and Tim Lisko)
Vulnerability management has existed since the birth of cybersecurity as an industry. As new vulnerabilities are discovered, enterprises have to determine if they are affected and then remediate those issues programmatically. Over the years, things have gotten way more complicated than simply fixing issues when they arise. The growth in the number of CVEs discovered each year has become overwhelming. To make matters worse, security teams have no way to properly prioritize the fixes without severely impacting the output of the business as a whole.
Enterprise security groups need a better way to create urgency for remediation within their engineering and development teams without being perceived as the group slowing down business. Enter the concept of “security debt.” Much like financial or technical debt, security debt can be measured by adding context to the decision tree for recommended remediation time and then adding a time element (let’s call this “security interest”) to the equation so that the longer issues remain, the more security debt is accumulated. DigitalOcean security leaders Ari Kalfus and Tim Lisko wrote a very interesting blog post outlining how they are working towards implementing a security debt metric at their firm. It’s a fantastic read, and I love the innovation around metrics. We can adapt this type of math to many more fields, and I look forward to seeing how this grows over time.
A Cybertruck War Machine Is A BAD Idea
A Chechen warlord, Ramzan Kadyrov, has acquired a Tesla Cybertruck and mounted it with a massive machine gun on the back. Please try to ignore any discussion or implication to the actual conflict in Ukraine and give this video a watch simply for the stupidity that is a Cybertruck with a machine gun. There are TONS of Cybertruck fails on YouTube and after you watch this video, go check out this one that features an old-school pickup truck saving the day when a cybertruck gets STUCK!
Quick Hits and Hidden Gems
Watch How a Hacker’s Infrared Laser Can Spy on Your Laptop’s Keystrokes (Wired) - Sam Kamkar of MySpace Worm fame resurfaces a legend from the 90s and brings it to life! I’ve been “hearing this for decades.” Now it’s real.
Meet AI Goat: The First Open Source AI Security Learning Environment Based on the OWASP Top 10 ML Risks (Orca Security) - An exciting environment for learning about AI security. While I like education, I’m more interested in the “how” to secure it problem.
Fuzzing Bests Formal Verification (Dan Guido) - Super technical yet awesome. I guess my formal methods courses really were an annoying waste of time! Long Live “ZED!”
If you’ve made it this far, you either found our musings at least semi-entertaining, OR you enjoyed the pain and kept going regardless. No matter how you made it to this point, you should know that we appreciate you. Please do us a solid and share The Cyber Why with your friends. We would love to reach a bigger audience, and referrals are how we do it. Help us out, and we’ll see you next week!