Happy “try not to explode your fingers” week! That’s right, it’s the fourth of July and The Cyber Why is here to bring you all the cyber news that will “blow” your mind! This week the TCW crew reminisces about the first time we saw a web browser, discusses how GTM in cyber is different, generative AI breaks reality, Cloudflare gives the finger to AI crawlers, and a wake boarding beer drinking gem from the great Zuck! All this and more in this week’s The Cyber Why!
The Cyber Why POD - Now in 4k! (To be fair, it always has been in 4k and high-quality audio. We’re tech nerds like that.)
TCW Newsletter and the TCW Podcast both have a few 2024 sponsorship slots remaining! If you are interested in reaching nearly 5k security-minded people a week via direct mail plus nearly 30K views per month, sponsor The Cyber Why. It’s inexpensive - I SWEAR! Email tyler.shields@gmail.com for more information.
Marc Andreessen and the History of Netscape
The true story -- as best I can remember -- of the origin of Mosaic and Netscape (Marc Andreessen Substack)
I’m a sucker for historical content. I love documentaries, historical data analysis, and learning about the past to help us with the future. I specifically remember the first time I saw a “web browser”. It was the Mosaic browser on a Sun SPARC Station in 1993. I was freshman at the Rochester Institute of Technology and one of my classmates loaded up Mosaic to introduce me to the “World Wide Web”. I was simultaneously amazed and bored. It was super cool to have interesting data at your fingers tips yet a total waste of time because it was impossible to find anything of real value (this was pre search engines). Essentially it felt a lot like ChatGPT does today! If you are into the history of the Internet, check out this great content on the “true story of the origin of Mosaic and Netscape.”
Go To Market in Cyber is Just DIFFERENT!
Cybersecurity technology adoption cycle and its implications for startups and security teams (Venture In Security)
Another excellent article from Ross Haleliuk from Venture in Security. This time with the help of Kane Narraway, Ross breaks down the cybersecurity adoption cycle and how it is reversed from the more common model as seen in non-cyber markets. Ross and Kane are right on with their analysis, specifically helping security teams understand how the dynamics of emerging technologies should work in their organization and what it really takes to be a design partner of innovative companies and technologies. They take a very buyer-centric view into the adoption cycle giving direct guidance on how security teams can mature over time.
I have seen this model from the other side of the coin for over a two decades. As an early go to market executive at both Signal Sciences and JupiterOne, I saw the vendor side of their framework play out. Early adopters of both companies were the highly mature security programs that had security engineering teams and the ability to take raw technology and mold it to their requirements. As the products we were building became more feature complete we were able to move downward to the design partner and early adopter segments of the curve. Generally this meant breaking open the finance and banking verticals. Finally, the hardest group to sell to was what I called the “mass buyer.” This buyer was almost always way less advanced in their cyber program and needed a specific set of features to make the technology usable to their low resourced and limited skill sets teams.
This is a great article to read and comprehend for both cybersecurity buyers as well as those companies looking to build a go to market engine.
Could Generative AI Break Reality - YES!
Google Says AI Could Break Reality (404 Media)
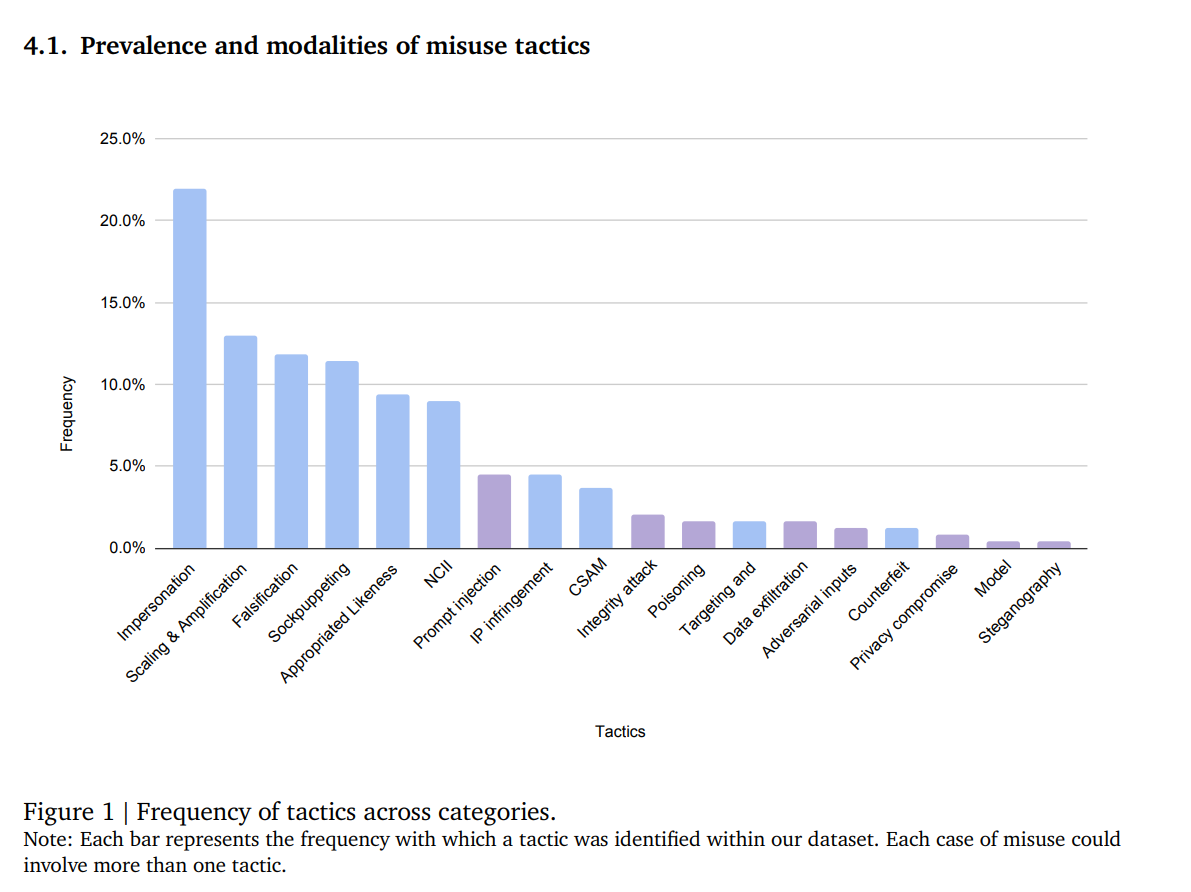
Generative AI Misuse: A Taxonomy of Tactics and Insights from Real-World Data (ARXIV.org)
A new paper written by a combination of research team members from Google’s multiple labs reviewed over 200 incidents of genAI misuse between January 2023 and March of 2024. The results of the research indicate that the majority of attacks against generative AI are not technically “hacks” of the system itself, but instead are much more focused on abusing the features that exist for malicious behavior or alternative methods of reward. The analysis shows that the prevalence of misuse tactics center on impersonation, scaling and amplification of malicious content, falsification of data, and sockpuppeting. The team at 404 Media did a great job breaking down where the gaps exist in the research (small n, classification issues, etc) but at the end of the day they (and I) are fairly confident that the recommendations and findings are directionally accurate. If these types of attacks continue to propagate unabated, the concept of what “reality really is” can indeed morph, or at least be skewed, in order to achieve the attackers intent. It’s not about attacking the LLM, or input injection, or poisoning the AI data set - it’s really about abusing the general input and output content in enough volume to make an alternative reality become the norm. How’s that for some real matrix style shit!
Cloudflare Shoots Across the Bow of AI Crawlers
Cloudflare goes to war with Microsoft, Google, and OpenAI's bots, with blanket free tools to block all crawlers (Windows Central)
Keeping with the theme of “independence,” Cloudflare just released a free tool to help content creators declare “AIdependence.” (OK, first of all the pun doesn’t even make sense. It was definitely forced.. #fail++.) The technology launch comes on the back of the Microsoft AI chief last week saying that “public content on the open web is freeeware.” In response, Cloudflare created new features that allow customers, even those on the free tier, to block their content from all AI crawlers and bots.
I’m struggling with this concept. As a content creator myself, isn’t the whole point of writing to have a human being consume the output? In the new world, driven by AI systems, the concept of readers doing traditional Google searches for your content will fade away. Instead of going direct to the source pages readers will consume the bulk of their content from some type of aggregation algorithm that is AI derived. It’s already happening with short form video content via the TikTok and YouTube short systems. As an author, if I want my writing to continue to be discovered I have to let the search systems of the 21st century (AI system crawlers) find my content. Isn’t this somewhat like telling Google to not index your content back in 1999. It may have felt like the right thing to do at the time but the end result would have been your content never being consumed by an audience. I believe this is what will happen here.
Check it out - I didn’t spill a DROP!
Mark Zuckerberg's Lake Tahoe antics are getting even weirder (SFGate.com)
To end this edition of The Cyber Why newsletter here’s something completely unexpected. The all powerful Zuck decided it would be social media worthy to don a tuxedo and an American flag and go wake boarding to the best 4th of July song in history - Born in the USA. This is a very high scoring frat boy activity. Zuck only lost points because he clearly didn’t properly utter the words “Hold my beer!” before he hopped on the board. Hats off to you Zuck - may all of your beers be a banquet!
Quick Hits and Hidden Gems
Gymnastics is the Turing test of video generation models (@deedydas) - This could have easily been a story #5. Apparently Gemini classifies this as sexual explicit material as well!
AI startup Abnormal Security is set to be valued at $5 billion in new funding round, sources say (Business Insider) - That’s a LOT of cheddar. The pace of that treadmill just jumped another few miles per hour. Keep running hard Abnormal!
6 Things To Know About Getting Acquired: The Good, The Bad, The Somewhat Ugly (Jason M. Lemkin) - I have been giving similar tips to founders for years. These are things many first time founders don’t know about M&A.
A Eulogy for DevOps (Mathew Duggan) - An interesting tear down of DevOps explaining why it was doomed to fail from the get go. Comment below!
If you’ve made it this far, you either found our musings at least semi-entertaining, OR you enjoyed the pain and kept going regardless. No matter how you made it to this point, you should know that we appreciate you. Please do us a solid and share The Cyber Why with your friends. We would love to reach a bigger audience, and referrals are how we do it. Help us out, and we’ll see you next week!